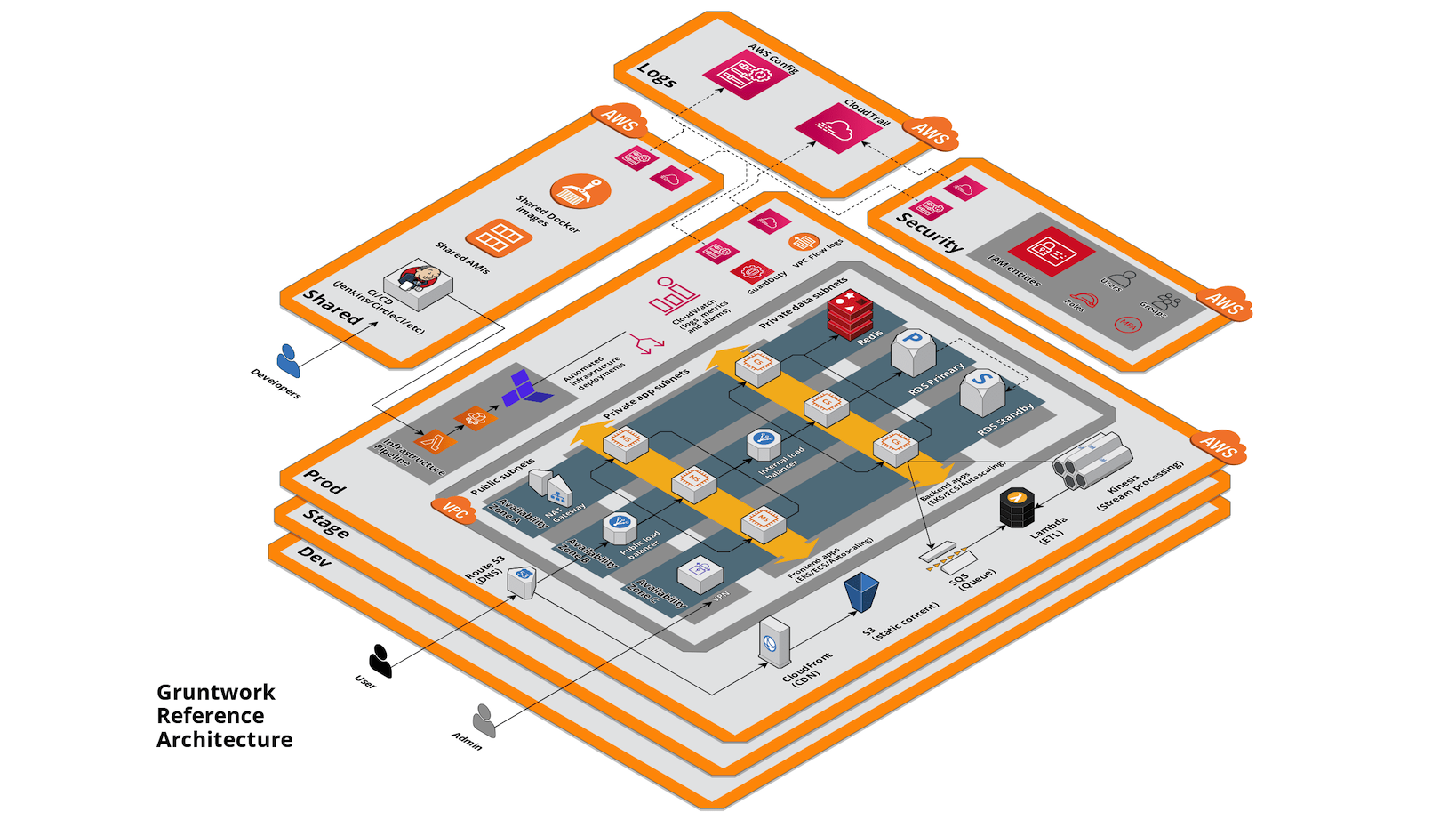
A new standard for architecture
The Reference Architecture is an opinionated, battle-tested, best-practices way to assemble the code from the Infrastructure as Code Library into an end-to-end tech stack that includes just about everything you need: server cluster, load balancer, database, cache, network topology, monitoring, alerting, CI/CD, secrets management, VPN, and more (check out the Production Readiness Checklist to see what it takes to go to prod).
We generate the Reference Architecture based on your needs, deploy into your AWS accounts, and give you 100% of the code. Since you have all the code, you can extend, enhance, and customize the environment exactly according to your needs. The deploy process takes about one day. Contact Us to set up a demo!
We also offer a CIS AWS Foundations Benchmark compliant version of the Reference Architecture. See our Compliance offering to learn more.
Get a Detailed Walkthrough of the Reference Architecture Account Structure
See our guide
How to configure a production-grade AWS account structure using Gruntwork AWS Landing Zone.
How It Works
Choose your architecture options
Customize your architecture and complete a few setup steps:
- Create several AWS accounts (logs, security, shared, dev, stage, and prod)
- Choose a region
- Set up domains in DNS
- Run services on Docker using EKS (Kubernetes) or ECS, or directly on EC2 Instances using ASGs
- PostgreSQL, MySQL, SQL Server, Aurora, or other relational database
- Redis or Memcached
- CircleCI, GitLab, or Jenkins
- Bastion Host or OpenVPN
- Static content storage and serving
- Serverless functions
- DNS, TLS
- Monitoring, Alerting, Log Aggregation
We build your architecture
We generate the architecture using Terragrunt, Terraform, Bash, Python and Go. We deploy the resources to your AWS accounts. We validate the configuration, then we push the code to your git repository. For AWS, this takes about one day.
Learn how to use it
Use our DevOps Training Library to learn how to use your new architecture with a series of micro-videos that do an in-depth walkthrough of all the most common uses cases. Need to learn Terraform, Docker, or Packer? We have courses on those, too!
Get support
If you run into a snag, ask a question on our community support channel via Slack. Or sign up for Professional Support to chat directly with Gruntwork engineers via a private shared Slack channel or email, and guarantee a timely response.
Reference Architecture Features
Infrastructure as Code
Written in Terraform, Go, Python, and Bash. You get 100% of the code.
Production-ready
The architecture has been proven with hundreds of Gruntwork customers.
Fast
We'll deploy a fully-working, best-practices tech stack in AWS in about one day!
Reliable
Designed for high availability, scalability, and durability
Secure
Account-level segmentation, centralized audit trail, network segmentation, encrypted by default, server hardening, & more
Documented
Includes training videos and documentation
What's included
The Reference Architecture includes:
| Account configuration | A best practices multi-account set up using Gruntwork Landing Zone for AWS. |
|---|---|
| Network Topology | For each environment, create a VPC with multiple subnet tiers, route tables, NAT Gateways, Network ACLs, Flow logs, etc. |
| Server cluster | Choose from a Docker Cluster (backed by Amazon EC2 Container Service or Amazon EC2 Kubernetes Service) or Auto Scaling Groups. |
| Load balancer | Public AWS Application Load Balancer for customer-facing services, and private ALBs for internal services. |
| Database | Choose a supported RDS database, such as Aurora, MySQL, PostgreSQL, MariaDB, Oracle, or SQL Server. |
| Cache | Choose a Redis or Memcached distributed Elasticache cache cluster. |
| Static content | Deploy your images, CSS, and JS into an S3 bucket and configure a CloudFront CDN in front of it. |
| Bastion host | Choose from either a plain Linux host or an OpenVPN server as a remote access network bastion. |
| CI server | Choose from Jenkins, CircleCI, or GitLab. |
| Sample frontend app | A sample frontend application that shows how to package the code using Docker or Packer, how to manage configuration across multiple environments, how to store application secrets, how to do service discovery to talk to a backend app, and how to run the entire stack in the dev environment. |
| Sample backend app | A sample backend application that shows how to package the code using Docker or Packer, how to manage configuration across multiple environments, how to store application secrets, how to talk to the database and cache, and how to apply schema migrations. |
| Serverless | Optionally deploy serverless functions using Terraform. |
| Environments | Choose the isolated environments you want to create: e.g., dev, qa, stage, prod. |
|---|---|
| Encryption | Encryption is enabled by default, including encrypted AMIs, EBS volumes, TLS certificates via AWS Certificate Manager, and everywhere else. |
| Infrastructure pipeline | Set up a workflow for infrastructure code using Gruntwork Pipelines. |
| Automated build & deployment (CI / CD) | Run a build after every commit to test your code, package it using Docker or Packer, and, for commits to certain branches or tags, automatically deploy that Docker or Packer image to specific environments. |
| Monitoring | Configure metrics in CloudWatch. |
| Alerting | Configure alerts on key metrics: e.g., high CPU usage on EC2 instances, too many 4xx or 5xx errors on load balancers, low disk space on your database. |
| Log aggregation | Centralize all server logs in CloudWatch Logs for easier searching and filtering. |
| DNS | Configure your domain name(s) using Amazon Route 53. |
| SSL/TLS | Create SSL/TLS certificates for your domain names. |
|---|---|
| Server hardening | Configure every server to run fail2ban and to automatically install critical security patches on a nightly basis. |
| SSH management | Install ssh-grunt on every server, which allows admins to grant or revoke SSH access using your identity provider (e.g., IAM, Google, Active Directory) and for each developer to be able to use their own username and SSH key to connect to servers. |
| Secrets management | Use Secrets Manager to securely encrypt and decrypt application secrets, such as database passwords. |
| Account security | Enable centralized audit logging for all of your API calls. Create best practices IAM groups and policies for user and permissions management. |
| Threat detection | Use Amazon GuardDuty to monitor for malicious and unauthorized behavior in your environment. |
| Resource configuration | Enable AWS Config with a best practices set of Config Rules to monitor for anomalous behavior. |
| High Availability | All aspects of the architecture are designed for high availability: e.g., all servers are deployed across multiple Availability Zones; load balancers perform health checks and automatically replace failed servers; the load balancers themselves run multiple servers and do automatic failover; the database and cache can also do automatic failover to standby servers in another Availability Zone; data is automatically backed up on a nightly basis. |
|---|---|
| Scalability | All aspects of the architecture support easy vertical and horizontal scalability: auto scaling policies resize the server cluster in response to load; the load balancers will automatically scale up and down in response to load; you can configure read replicas for your database and cache clusters. |
| Infrastructure as code | You get 100% of the source code for everything in the Reference Architecture. It is written using a variety of tools, including Terragrunt, Terraform, Packer, Docker, Go, Python, and Bash. |
| Built for teams | With Gruntwork Pipelines, every change is centralized, peer-reviewed, and audited, all using code. Use the pipeline for your infrastructure and application deployments! |
| Documentation | Comprehensive written and video documentation of everything included in the Reference Architecture. |
Read our blog post How to Build an End to End Production-Grade Architecture on AWS for an overview of what is included.
Pricing
Check out the Pricing page for details. Please note that to use the Reference Architecture, you must be a Gruntwork Subscriber.